Outline:
- Introduction
- User Data Security in Web and App Development: A Crucial Step
- Overview of User Data Security
- Common Security Threats in Web and App Development
- Malware and Ransomware Attacks
- Cross-Site Scripting (XSS)
- SQL Injection
- DDoS Attacks
- Best Practices for Web and App Security
- Regular Software Updates
- Strong Password Policies
- Secure Data Encryption
- Two-Factor Authentication (2FA)
- Importance of Data Privacy Policies
- GDPR and Its Implications
- CCPA and User Rights
- Secure Coding Practices
- Input Validation
- Output Encoding
- Parameterized Queries
- The Role of HTTPS and SSL/TLS Certificates
- Encryption of Data Transmission
- Trust and Credibility
- User Education and Awareness
- Phishing Awareness Training
- Reporting Suspicious Activities
- Safe Online Behavior
- Mobile App Security
- Securing App Data
- User Permission Management
- Cloud Security Considerations
- Data Storage and Encryption
- Identity and Access Management
- Third-Party Integrations and Security Risks
- Vetted Partnerships
- Regular Security Audits
- Incident Response and Recovery
- Developing an Incident Response Plan
- Data Restoration and Recovery
- Testing and Auditing for Security
- Vulnerability Scanning
- Penetration Testing
- Balancing Security and User Experience
- Minimizing Friction for Users
- Providing Transparent Security Measures
- Future Trends in Web Design & Development in UAE and App Security
- Artificial Intelligence in Security
- Blockchain Technology and Decentralization
- Conclusion
Protecting Web and App Development: User Data Security
In today’s Graphic Design in UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount. Moreover, with increasing cybersecurity threats and constant breaches of personal information, protecting user data has become both a moral and legal obligation for Web Design & Development in UAE and app developers.
-
Introduction to user data security
The introduction of any Web Design & Development in UAE or mobile application should highlight the critical importance of security in the development process. As technology advances, so do the tactics of cybercriminals who are constantly seeking vulnerabilities to exploit. Additionally, the article aims to shed light on the essential security measures that developers must implement to safeguard user data effectively.
-
Common Security Threats in Web and App Development
The Digital Marketing in UAE landscape is fraught with various security threats. Therefore, developers need to be aware of them to build robust and secure applications for user data security.
Malware and Ransomware Attacks
Malware and ransomware attacks are malicious software programs Web Design & Development in UAE to infiltrate systems, encrypt data, and demand ransom for its release. Consequently, developers must employ antivirus software and keep systems updated to mitigate these threats.
Cross-Site Scripting (XSS)
A vulnerability known as cross-site scripting enables attackers to insert malicious programs into web pages that are being viewed by other users. Therefore, developers should validate and sanitize user input to prevent XSS attacks.
SQL Injection
SQL Injection involves inserting malicious SQL code into applications to gain unauthorized access to databases. Additionally, developers should utilize parameterized queries to prevent this vulnerability.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks overwhelm servers with a flood of requests, rendering the application unavailable. Therefore, implementing DDoS protection measures is crucial to maintaining service availability.
-
Best Practices for User Data Security for Web Design & Development in UAE and App Security
Developers can follow several best practices to enhance User Data Security in their web and mobile applications.
Regular Software Updates
Regularly updating software, frameworks, and libraries ensures that known vulnerabilities are patched, reducing the risk of exploitation.
Strong Password Policies
Enforcing strong password policies, such as complexity requirements and regular password changes, helps prevent unauthorized access.
User Data Security Encryption
Encrypting sensitive user data security during transmission and storage adds an extra layer of protection against data breaches.
Two-Factor Authentication (2FA)
Implementing 2FA adds an extra layer of security, requiring users to provide a second form of identification during login.
-
Importance of User Data Security: Privacy Policies
Data privacy policies are essential for building trust with users and complying with relevant data protection regulations to ensure User Data Security.
GDPR and Its Implications
The General Data Protection Regulation (GDPR) is a comprehensive data protection law that applies to businesses handling EU citizens’ data. Developers should understand its implications and comply accordingly.
CCPA and User Rights
The California Consumer Privacy Act (CCPA) grants California residents specific rights over their personal data. Adhering to CCPA requirements demonstrates a commitment to user privacy.
-
Secure Coding Practices
Writing secure code is crucial to minimizing vulnerabilities in web and app development. Additionally, it helps prevent potential exploitation by malicious actors.
Input Validation
Validating user input helps prevent malicious data from being processed, reducing the risk of code injection. Furthermore, it enhances the overall user data security posture of the application.
Output Encoding
Encoding output data prevents cross-site scripting attacks by rendering user-generated content safe for display. Additionally, it ensures that any potentially harmful code is neutralized before being presented to users.
Parameterized Queries
Using parameterized queries in database interactions prevents SQL injection by separating data from code. As a result, it becomes significantly more challenging for attackers to manipulate the query’s structure and exploit potential vulnerabilities.
-
The Role of HTTPS and SSL/TLS Certificates
User Data Securing transmission between users and servers is essential for maintaining confidentiality and trust.
Encryption of Data Transmission
HTTPS encrypts data during transmission, ensuring that sensitive information remains secure.
Trust and Credibility
Having a valid SSL/TLS certificate instills confidence in users by indicating a secure connection.
-
User Education and Awareness
Educating users about security risks and best practices empowers them to protect their data.
Phishing Awareness Training
Teaching users to identify and avoid phishing attempts helps prevent social engineering attacks.
Reporting Suspicious Activities
Encouraging users to report suspicious activities enhances the application’s overall security.
Safe Online Behavior
Promoting safe online behavior, such as logging out after sessions, minimizes potential risks.
-
Mobile App Security
Securing mobile apps requires additional considerations due to the nature of device usage.
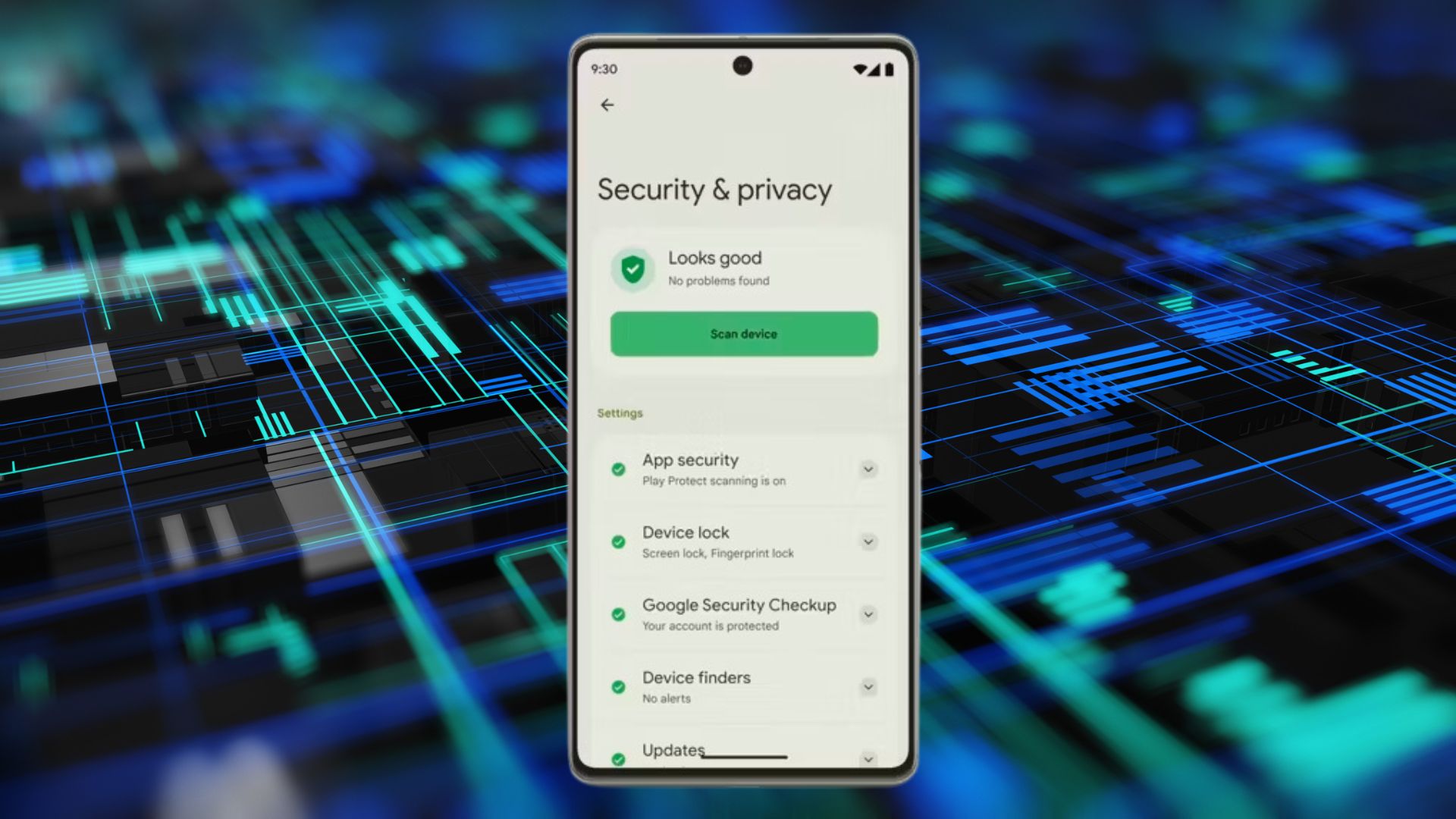
Securing App Data
App data should be encrypted, and access permissions must be carefully managed.
User Permission Management
Apps should request permissions only when necessary to protect user privacy.
For applications hosted in the cloud, developers need to address specific security aspects. Firstly, they must ensure proper authentication and access controls to safeguard sensitive data. Secondly, implementing encryption measures for data at rest and in transit helps maintain confidentiality.
Data Storage and Encryption
Selecting secure cloud storage and encrypting data ensures confidentiality. Moreover, it adds an extra layer of protection to sensitive information, making it unreadable to unauthorized individuals.
Identity and Access Management
Proper identity and access management prevent unauthorized access to cloud resources. Additionally, it ensures that only authenticated and authorized users can interact with sensitive data and applications.
-
Third-Party Integrations and Security Risks
Third-party integrations can introduce vulnerabilities if not thoroughly vetted. For instance, poorly secured APIs or plugins may provide potential entry points for attackers. As a result, conducting comprehensive security assessments of these integrations is essential to identify and address any potential risks.
Vetted Partnerships
Collaborating with reputable and secure third-party vendors minimizes risks. Furthermore, it ensures that the products or services provided meet high-security standards. Additionally doing so, organizations can enhance the overall security of their systems and applications.
Regular User Data Security Audits
Conducting periodic security audits of third-party integrations helps identify potential weaknesses. Additionally, it allows organizations to proactively address any security issues that may arise. Further regularly reviewing the security measures of these integrations, companies can maintain a higher level of confidence in their overall security posture.
-
Incident Response and Recovery
Developing a robust incident response plan is crucial for handling security breaches effectively. Moreover, it ensures that the organization is well-prepared to respond promptly and efficiently when a breach occurs. Further outlining clear procedures and responsibilities, the incident response plan helps minimize the impact of the breach and facilitates a coordinated and effective response.
Developing an Incident Response Plan
Having a well-defined plan in place ensures a swift and organized response to security incidents. Additionally, it helps avoid confusion and delays in critical moments. Moreover establishing clear guidelines and communication channels, the incident response plan enables stakeholders to act promptly and effectively in mitigating the effects of the security incident.
Data Restoration and Recovery
The ability to restore data after an incident is vital to minimize the impact on users. Furthermore, it allows businesses to resume normal operations more quickly, reducing downtime and potential financial losses. Additionally having robust data backup and recovery procedures in place, organizations can ensure that essential information remains accessible and intact even in the face of security incidents.
-
Testing and Auditing for User Data Security
Thorough testing and auditing of applications identify and rectify potential security flaws. Additionally, these processes help ensure that applications meet the required security standards and adhere to best practices. Further conducting comprehensive tests and audits, developers can proactively address vulnerabilities, reducing the risk of security breaches and data compromises.
Vulnerability Scanning
Automated vulnerability scanning helps identify weak points in applications. Moreover, it efficiently detects potential security gaps and misconfigurations that might otherwise go unnoticed. Additionally automating this process, developers can conduct regular and systematic assessments, enabling them to address vulnerabilities promptly and proactively improve the overall security posture of their applications.
Penetration Testing
Ethical hacking through penetration testing simulates real-world attacks to uncover vulnerabilities. Additionally, it provides valuable insights into the security strengths and weaknesses of an application. Moreover conducting controlled and authorized hacking attempts, organizations can proactively identify and address potential security flaws before malicious hackers exploit them.
-
Balancing User Data Security and User Experience
While security is paramount, developers must strike a balance to avoid negatively impacting user experience. Additionally, implementing stringent user data security measures should not come at the cost of usability or convenience for users. Moreover carefully considering user needs and expectations, developers can create secure applications that offer a seamless and enjoyable user experience.
Minimizing Friction for Users
Ensuring security measures do not create unnecessary inconvenience for users is crucial. Moreover, striking a balance between security and usability is essential to maintain a positive user experience. Additionally carefully Web Design & Development in UAE and implementing security features, developers can enhance the application’s protection without imposing undue burdens on users.
Providing Transparent Security Measures
Being transparent about security practices builds trust with users. Additionally, it demonstrates the organization’s commitment to safeguarding their data and privacy. Further openly sharing information about security measures, data handling processes, and compliance with relevant regulations, companies can establish credibility and foster a stronger relationship with their user base.
-
Future Trends in Web and App Security
Technology continues to evolve, and new security trends emerge to combat evolving threats. Moreover, cybersecurity professionals must stay vigilant and adapt their strategies to address the latest challenges effectively. Additionally embracing emerging security technologies and practices, organizations can better defend against sophisticated cyberattacks and safeguard their valuable assets and information.
Artificial Intelligence in User Data Security
AI-powered security solutions can proactively detect and respond to threats. Additionally, these advanced technologies use machine learning algorithms to analyze vast amounts of data and identify patterns indicative of potential security breaches. Moreover automating threat detection and response processes, AI empowers organizations to mitigate risks faster and more efficiently, strengthening their overall cybersecurity posture.
Blockchain Technology and Decentralization
Blockchain’s decentralized nature offers enhanced security for certain  applications.Moreover, this distributed ledger technology ensures that data is stored across a network of nodes, making it extremely difficult for malicious actors to tamper with information or gain unauthorized access. Additionally leveraging blockchain’s inherent features, applications can achieve a higher level of data integrity and transparency, particularly in fields like finance, supply chain management, and identity verification.
applications.Moreover, this distributed ledger technology ensures that data is stored across a network of nodes, making it extremely difficult for malicious actors to tamper with information or gain unauthorized access. Additionally leveraging blockchain’s inherent features, applications can achieve a higher level of data integrity and transparency, particularly in fields like finance, supply chain management, and identity verification.
-
Protecting Against Emerging Threats
As technology evolves, new security threats emerge, challenging developers to stay ahead of potential risks.
Internet of Things (IoT) Vulnerabilities
The proliferation of IoT devices introduces new security challenges, as interconnected devices can be exploited if not adequately secured.
Biometric Security Concerns
While biometric authentication offers convenience, developers must address potential vulnerabilities and ensure the protection of biometric data.
-
The Human Factor in User Data Security
Despite robust technical measures, human errors and social engineering remain significant security risks.
Employee Training and Awareness
Educating employees about cybersecurity best practices can prevent unintentional data breaches and ensure a security-conscious workforce.
Social Engineering Awareness
Recognizing social engineering tactics empowers employees to detect and avoid manipulation attempts.
-
Data Breach Mitigation and Response
Even with stringent security measures, data breaches can occur. Consequently, necessitates an effective response plan.
Identifying the Source
Swiftly identifying the source of the breach helps contain and limit its impact. Additionally, it enables organizations to take appropriate actions to prevent similar incidents in the future.
Notifying Affected Users
Transparently communicating with affected users about the breach fosters trust and helps them take necessary precautions. Moreover, it demonstrates the organization’s commitment to its customers’ security and privacy.
-
Compliance and Legal Considerations
Developers must comply with relevant laws and regulations governing data protection and user privacy. Additionally, adhering to these legal requirements is essential to avoid legal liabilities and penalties. Moreover staying informed about the evolving data protection landscape, developers can ensure that their applications and systems align with the necessary standards and safeguards for handling user data responsibly.
HIPAA (Health Insurance Portability and Accountability Act)
For healthcare-related applications, adhering to HIPAA regulations is crucial to safeguarding sensitive patient data. Moreover, it ensures that the privacy and security of individuals’ health information are protected as required by law. Additionally following HIPAA guidelines, developers can build trust with users and healthcare providers, demonstrating their commitment to maintaining the confidentiality and integrity of patient data.
Payment Card Industry Data Security Standard (PCI DSS)
Developers handling payment card information must comply with PCI DSS to protect cardholder data. Additionally, adhering to these standards is essential for ensuring the security and integrity of financial transactions. Moreover implementing the necessary security measures and controls, developers can minimize the risk of data breaches and unauthorized access to sensitive payment card information.
-
The Future of User Data Security
As technology continues to advance, the future of web and app security promises innovative solutions to combat emerging threats. Furthermore, advancements in artificial intelligence and machine learning offer the potential to enhance threat detection and response capabilities. Additionally staying abreast of these developments and incorporating cutting-edge security practices, developers can better protect users and their data from evolving cybersecurity challenges.
Quantum Cryptography
Quantum cryptography offers unhackable encryption, revolutionizing data protection in the digital age. Additionally, this groundbreaking technology leverages the principles of quantum mechanics to create secure communication channels immune to traditional hacking methods. Moreover harnessing the power of quantum entanglement and superposition, quantum cryptography holds the potential to redefine the landscape of cybersecurity, providing unprecedented levels of data privacy and integrity.
Behavioral Biometrics
Using behavioral patterns for user authentication enhances User Data Security while ensuring a seamless user experience. Moreover, this approach analyzes user behavior, such as typing speed, keystroke patterns, and device usage, to establish unique biometric profiles. Further continuously monitoring these behavioral traits, organizations can detect anomalies and potential unauthorized access attempts in real time, fortifying their authentication processes without burdening users with additional authentication steps.
Google Authenticator
Google Authenticator is the sentinel of Digital Marketing in UAE security. It’s a two-factor authentication app that safeguards online accounts. By generating time-based verification codes, it adds an extra layer of protection beyond passwords. Users enter these codes during login, enhancing security against unauthorized access. Google Authenticator fortifies accounts on various platforms, from email to financial services, deterring phishing and hacking attempts. With its seamless setup and offline capabilities, Google Authenticator empowers individuals to take control of their Digital Marketing in UAE identities, fostering a safer online environment where personal information remains confidential.
The OWASP Top 10
The OWASP Top 10 stands as a beacon in the realm of cybersecurity. It’s a meticulously curated list that highlights the most critical web application security vulnerabilities. From injection attacks to broken authentication, these vulnerabilities are the gateway to data breaches and cyber threats. By shedding light on these common pitfalls, OWASP Top 10 guides developers, security professionals, and businesses to prioritize mitigation efforts. This collective wisdom empowers Digital Marketing in UAE landscapes with robust defenses, ensuring that websites and applications stand resilient against evolving cyber risks, ultimately fortifying the foundation of trust in the digital age.
Google 2-Step Verification
Google 2-Step Verification stands as a guardian of Digital Marketing in UAE access. It adds an extra layer of security to Google accounts, beyond just passwords. Once enabled, users need to provide a verification code in addition to their password during login. This code is generated on a user’s smartphone, adding an element of possession to the authentication process. Google 2-Step Verification combats unauthorized access and phishing attempts, making it significantly harder for attackers to breach accounts. It’s a simple yet powerful tool that empowers users to take control of their online security and safeguard their personal information.
Web application security
Web application security is the Digital Marketing in UAE armor that shields against cyber threats. It’s the proactive strategy of safeguarding web applications from vulnerabilities and attacks. From code injection to cross-site scripting, web application security encompasses measures that ensure confidentiality, integrity, and availability of data. By employing practices like input validation, encryption, and secure coding, it thwarts breaches and protects user information. Web application security is the sentinel that upholds user trust and brand reputation, creating a fortified digital environment where innovation and functionality coexist securely in the face of evolving cyber risks.
Key management in Cryptography
Key management in cryptography is the custodian of Digital Marketing in UAE secrets. It’s the practice of securely generating, distributing, storing and revoking cryptographic keys. These keys are the linchpin of data protection, enabling encryption and decryption processes. Effective key management ensures keys are accessible to authorized users while inaccessible to adversaries. It oversees their lifecycle, from creation to destruction, and enforces strong security protocols. By maintaining key confidentiality and integrity, key management fortifies the foundation of cryptography, guaranteeing the secrecy and authenticity of sensitive information in an interconnected world where data privacy is paramount.
Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) stand as the vigilant sentinels of online security. They shield web applications from cyber threats by analyzing incoming traffic and detecting and blocking malicious activities. WAFs leverage rule-based or AI-driven approaches to identify anomalies, safeguarding against attacks like SQL injection, cross-site scripting, and more. By monitoring HTTP requests and responses, WAFs ensure that only legitimate traffic reaches the application, mitigating the risk of data breaches and disruptions. In an interconnected landscape, WAFs are the frontline defense, creating a fortified barrier that safeguards both user data and business reputation from the ever-evolving realm of cyber threats.
Mobile authentication
Mobile authentication is the key to secure access on the go. It verifies users’ identities through mobile devices, adding a layer of security beyond passwords. Methods like biometrics, SMS codes, and mobile apps ensure reliable verification, granting users safe and convenient entry to Digital Marketing in UAE spaces while thwarting unauthorized access.
Conclusion
Security in web and app development is a continuous journey. By following best practices, adhering to data protection laws, and staying updated on emerging threats, developers can build applications that protect user data effectively. Prioritizing security not only safeguards users but also establishes trust and credibility for the application and the brand. In conclusion, security in web and app development is not an afterthought but an integral part of the entire process. By prioritizing user data protection and staying informed about emerging threats, developers can build applications that inspire trust and confidence among users. Implementing best practices, following data privacy laws, and addressing human factors in security is essential to create a safe Digital Marketing in UAE environment for users.
Protecting user data is not only a legal requirement but also a moral responsibility. As technology advances, the need for robust user data security measures becomes even more critical. By continually adapting to evolving threats and leveraging cutting-edge security technologies, developers can ensure the safety and confidentiality of user data in an ever-changing digital landscape.
FAQs
-
Why is user data security crucial in web and app development?
Security is crucial in web and app development because it protects user data from unauthorized access and potential breaches, safeguarding user privacy and building trust.
-
What are some common security threats in web and app development?
Common security threats include malware and ransomware attacks, cross-site scripting (XSS), SQL injection, and DDoS attacks.
-
How can developers enhance web and app security?
Developers can enhance security by implementing regular software updates, strong password policies, secure data encryption, and two-factor authentication (2FA).
-
What role do data privacy policies play in web and app development?
Data privacy policies establish guidelines for handling user data, ensuring compliance with data protection regulations like GDPR and CCPA.
-
What are some future trends in web and app security?
Future trends include the integration of artificial intelligence in security and the utilization of blockchain technology for enhanced data protection.
-
What are the emerging threats user data security in web and app?
7. How can developers mitigate the human factor in user data security?Developers can mitigate human errors and social engineering risks through employee training and awareness programs focused on cybersecurity.
8. What steps should developers take in the event of a data breach?
In the event of a data breach, developers should promptly identify the source. Furthermore, they should notify affected users and implement measures to prevent future breaches.
9. What legal considerations should developers be aware of regarding data protection?
Developers must be aware of relevant laws and regulations, such as HIPAA and PCI DSS, to ensure compliance and protect user data. Additionally, adhering to these legal requirements is crucial for safeguarding sensitive information and maintaining users’ trust.
10. What does the future of user data security in web and app security hold?
The future of user data security in web and app development will likely involve advancements in encryption, biometrics, AI-driven threat detection, and stricter regulatory compliance to protect against evolving cyber threats.

